Your Estate, Your Rules: A Proactive Approach to Planning Your Legacy

Estate planning. The term often conjures images of mahogany offices, dusty legal tomes, and discussions reserved only for the very wealthy or those late in life. This perception is not just inaccurate; it’s a dangerous form of procrastination. In reality, estate planning is not about preparing for death; it’s about being profoundly proactive in managing […]
Leaving a Legacy: How to Plan Your Estate Wisely

Leaving a legacy is about more than just dividing your assets after you’re gone. It is a profound act of love and responsibility that safeguards your loved ones, communicates your values, and preserves the fruits of your life’s work. A wise estate plan ensures your final wishes are honored, minimizes financial stress and conflict for […]
Wealth Transfer: A Modern Approach to Estate Planning

The “Great Wealth Transfer” is upon us, with trillions of dollars poised to shift hands across generations in the coming decades. This monumental shift is reshaping the very definition of estate planning. No longer a simple exercise in drafting a will and minimizing taxes, the modern approach to wealth transfer is a holistic, forward-thinking strategy […]
The Thoughtful Executor: Navigating Your Loved One’s Estate

Being named the executor of a loved one’s estate is an honor, a profound act of trust, and one of the most significant administrative tasks a person can undertake. It is also, invariably, a role cast during a time of grief. The “Thoughtful Executor” balances legal obligations with emotional sensitivity, ensuring their loved one’s final […]
Estate Planning 101: Securing Your Family’s Future

Estate planning. The phrase itself can feel overwhelming, conjuring images of complex legal documents, high-powered lawyers, and perhaps even a somber contemplation of one’s own mortality. It’s a topic many people know they should address but often push off until “later.” However, viewing estate planning as merely a post-mortem arrangement is a mistake. It is, […]
Protecting Your Assets: The Essentials of Estate Planning

The word “estate” often conjures images of vast wealth and sprawling properties, leading many to believe that estate planning is an exclusive concern of the ultra-rich. This couldn’t be further from the truth. If you own assets—a home, a car, a bank account, a retirement fund, or even personal belongings—you have an estate. And, fundamentally, […]
Planning for the Future: A Family’s Guide to Estates

For many families, discussing what happens after a loved one passes away can be uncomfortable. It’s a topic often shrouded in emotion and uncertainty. Yet, proactively planning for the future is one of the most loving and responsible acts a person can undertake. It provides clarity, reduces family conflict, and ensures that your wishes are […]
Beyond the Will: Comprehensive Estate Planning
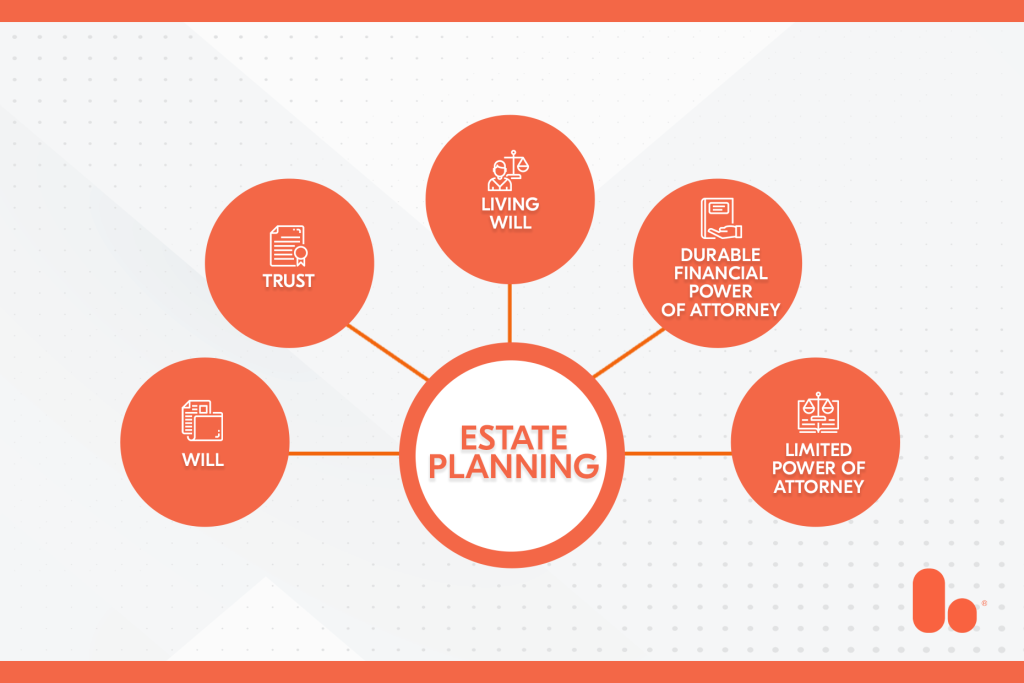
Many people equate estate planning with a single document: the will. While a will is a fundamental part of the process, it’s just one piece of a much larger puzzle. True comprehensive estate planning goes far beyond a simple will, creating a robust framework to manage your assets, protect your family, and ensure your wishes […]
Your Legacy, Your Plan: A Guide to Estate Planning

Many people avoid thinking about estate planning, often believing it’s something only the wealthy need to worry about, or that it’s a grim task best left for later. The truth is, estate planning is one of the most proactive and loving actions you can take for yourself and your family. It’s not just about what […]
Cybersecurity Policies and Frameworks: A Cornerstone of Modern Defense

In an era defined by digital transformation, the importance of robust cybersecurity cannot be overstated. From multinational corporations to small businesses and individual users, everyone is a potential target for an increasingly sophisticated array of cyber threats. While firewalls and antivirus software are essential tools, they are just one part of a comprehensive defense strategy. […]